Recently I’ve been looking into moving all the API connections we have in Logic Apps (Consumption) to use Managed Identities as much as possible. We had done the required configuration for Azure Key Vault connections before and we were expanding to other connectors as well.
Key Vault API Connection for Managed Identity
When we did for Azure Key Vault we came with the following structure below (Bicep format):
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 |
resource apiConnectionKeyVault 'Microsoft.Web/connections@2016-06-01' = { name: keyVaultApicName location: location properties: { displayName: keyVaultApicName api: { id: keyVaultApiReferenceId } parameterValueType: 'Alternative' alternativeParameterValues: { 'vaultName': keyVaultName } } } |
This structure is documented here, but it’s really hard to find and we actually end up founding the solution first in few blog posts around the community (sorry as I don’t remember where otherwise would have given the proper credit). The document being so hard to find is not ideal but at least is there.
Anyway, when we started to look how to do the Managed Identity API connection for Service Bus, we tried to use the same structure with parameterValueType as ‘Alternative’, but it didn’t work.
In the same document in the link above, it shows two ways of doing the authentication. One for ‘Single-authentication’ and the other for ‘Multi-authentication’, it took me some time to notice but there’s this link in the document that list which connectors use what. So far, I’ve spent already a good number of hours trying to find the right information. Again, not ideal.
Service Bus API Connection for Managed Identity
So, now that I know that for the Service Bus connector the API connection structure is different I went ahead and tried that out as below (Bicep format):
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 |
resource apiConnectionServiceBus 'Microsoft.Web/connections@2016-06-01' = { name: serviceBusApicName location: location properties: { displayName: serviceBusApicName api: { id: serviceBusApiReferenceId } parameterValueSet: { name: 'managedIdentityAuth' values: {} } } } } |
So, the API connection is created but it does not work as there is missing information. So I went to try to find any document that talks about what are the custom properties per connector (in my case Service Bus) that I needed to pass in that values section or any other place. Zip, zero, zilch, nada. This time not even in blogs I found this information.
I tried to export the ARM template from the portal but what it generates does not contain anything about that configuration we saw above as you can see below:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 |
{ "type": "Microsoft.Web/connections", "apiVersion": "2016-06-01", "name": "[parameters('name')]", "location": "australiaeast", "kind": "V1", "properties": { "displayName": "[parameters('name')]", "statuses": [ { "status": "Ready" } ], "customParameterValues": {}, "createdTime": "2022-04-26T05:01:35.3113753Z", "changedTime": "2022-04-27T03:30:51.6940078Z", "api": { "name": "servicebus", "displayName": "Service Bus", "description": "Description...", "iconUri": "/icon.png", "brandColor": "#c4d5ff", "id": "/subscriptions/.../managedApis/servicebus", "type": "Microsoft.Web/locations/managedApis" }, "testLinks": [] } } |
When I was almost giving up, I saw this little link in the API connector page ‘JSON View’. I never noticed that link before this work, so no idea how it has been there, but it solved my problem, saying exactly what was the structure that I need to create to be able to create the connection properly as you can see below (portal image and bicep format):
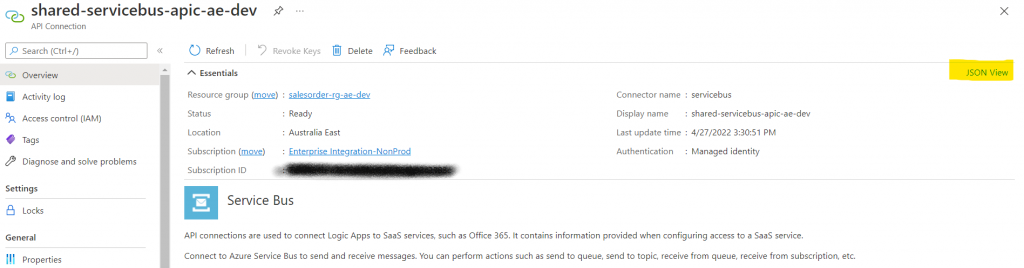
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 |
resource apiConnectionServiceBus 'Microsoft.Web/connections@2016-06-01' = { name: serviceBusApicName location: location properties: { displayName: serviceBusApicName api: { id: serviceBusApiReferenceId } parameterValueSet: { name: 'managedIdentityAuth' values: { namespaceEndpoint: { 'value': serviceBusNamespaceEndpoint } } } } } |
The value the namespace endpoint needs to be ‘sb://<Service Bus namespace>’. And voila, the API connection was created successfully and I just needed to give permissions to the managed identity to be able to access the Service Bus I wanted.
Permissions on Topics, Queues and Subscriptions
When I went to configure the permission, I started with the Azure Portal and since there’s an Access Control option for Topics (this is where I wanted to apply the permissions), I went with that. But whenever I chose the managed identity, it was being applied to the whole Service Bus and not only that Topic.
Tracing messages and Azure Service Bus monitoring across multiple Queues and Topic Subscriptions get powerful toolsets and actionable insights to troubleshoot messaging issues.
A little bit more investigation (at least this time it was easier to find), I found this documentation that says that Azure Portal does not support the assignment of permissions to queues, topics or subscriptions, and the way to do this is via CLI as you can see below:
|
1 2 3 4 |
az role assignment create \ --role $service_bus_role \ --assignee $assignee_id \ --scope /subscriptions/$subscription_id/resourceGroups/$resource_group/providers/Microsoft.ServiceBus/namespaces/$service_bus_namespace/topics/$service_bus_topic/subscriptions/$service_bus_subscription |
Summary
Since it has been sometime that Managed Identity is available for some connectors, I was expecting to have better, more complete and easier to find documentation, but that’s not the case. I spoke with one of the Logic Apps PM and hopefully there will be some adjustments on the documentation to make our life easier.
So, that’s it for this topic and I hope you guys enjoy it.
Cheers!!!


